Ghost File augments your existing security strategy, which may include network-based inspections for advanced threats and endpoint-based defense strategies. Think of Ghost File as a robust last line of defense, safeguarding your data stores in the event that ransomware bypasses your primary defenses (network and endpoint).
By using Ghost File, you can significantly reduce the blast radius of a ransomware attack, limiting its destructive impact and preserving the integrity of your data. This proactive defense mechanism removes your data stores from the list of potential ransomware targets, eliminating the necessity of reverting to backups for data recovery.
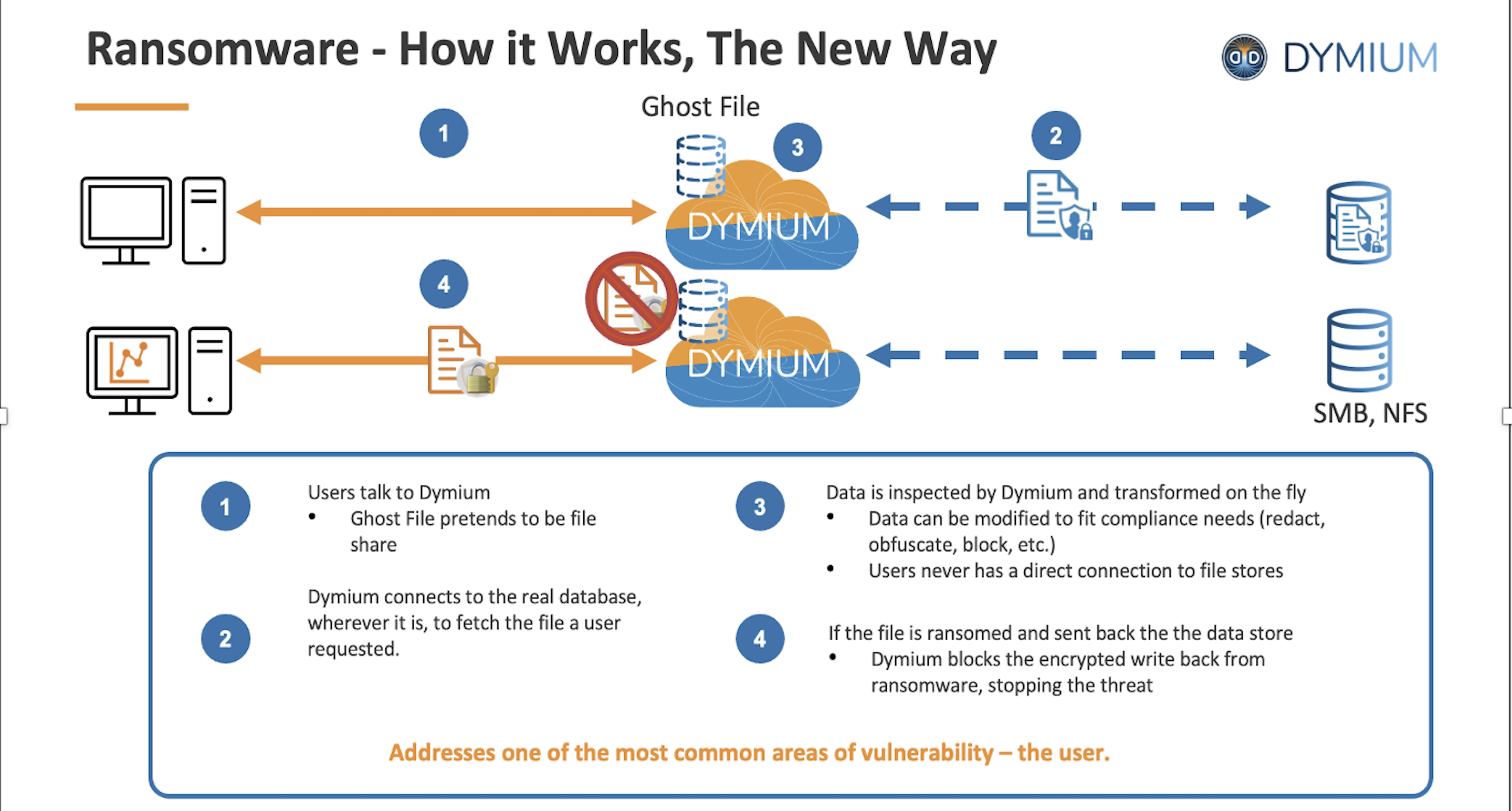
Dymium Ghost File acts as a protective layer in front of your enterprise data stores, adding a layer of ransomware threat prevention without being noticeable to users. It functions by mimicking the data store to users while securely fetching and returning data from your actual data stores through the Ghost File share. Ghost File intelligently monitors the nature of data access and the type of data being written back. If it detects encryption or cypher-based modifications typically associated with ransomware, Ghost File immediately blocks these malicious write-backs, effectively neutralizing the threat.
The solution eliminates the complexity, availability, and timeliness challenges of duplicating data into data warehouses or data lakes.
The solution also complements and easily integrates with existing IT infrastructure and other security solutions ensuring businesses can upgrade their cybersecurity without disrupting operations
It uniquely combines a zero trust architecture, centralized access policies, real-time, universal data translation services, and AI and machine learning, ensuring only authorized users can access the right data regardless of its location, while effectively preventing ransomware attacks
©2024 Dymium. All rights reserved.